I. Overview
II. How will Modern Authentication work and is this feature applicable to me?
III. Prerequisites to enable Modern Authentication in Exchange
IV. Steps to configure Modern Authentication in Exchange Server using ADFS as STS
V. Configure Exchange Server to use ADFS OAuth tokens
VI. Client-Side Modern Authentication configuration
VII. Test Outlook Client
Exchange Server 2019 CU13 부터는 ADFS를 활용하여 OAuth 2.0 (Modern Authentication) 을 지원하게 되었습니다.
Released: 2023 H1 Cumulative Update for Exchange Server - Microsoft Community Hub
여기서 포인트는 "ADFS 연결을 지원한다." 입니다. 그리고 ADFS는 Azure MFA를 포함한 다양한 3rd Party MFA를 지원합니다.
아래의 기술자료를 참고하여 작성하였습니다.
Enable Modern Auth in Exchange Server on-premises | Microsoft Learn
I. Overview
기술 자료에서는 우선 다음과 같이 설명하고 있습니다.
With the release of Exchange Server 2019 CU13, Exchange Server supports OAuth 2.0 (also known as Modern authentication) for pure on-premises environments using ADFS as a security token service (STS). This document provides the prerequisites and steps to enable this feature.
Exchange Server 2019 CU13 릴리스와 함께 Exchange Server는 ADFS를 STS(보안 토큰 서비스)로 사용하는 순수 온-프레미스 환경에 대해 OAuth 2.0(최신 인증이라고도 함)을 지원합니다. 이 문서는 이 기능을 활성화하기 위한 전제 조건과 단계를 제공합니다.
To use modern auth, users need clients (Outlook or any other native OS clients) that support Modern auth using ADFS. Initially, this feature is available only for Outlook on Windows, but support for modern auth will be added to other Outlook clients in the future.
최신 인증을 사용하려면 ADFS를 사용하는 최신 인증을 지원하는 클라이언트(Outlook 또는 기타 기본 OS 클라이언트)가 필요합니다. 처음에 이 기능은 Windows의 Outlook에서만 사용할 수 있지만 최신 인증에 대한 지원은 향후 다른 Outlook 클라이언트에 추가될 예정입니다.
기존에는 Outlook 연결시 Windows 인증 (기본인증)창으로 나타납니다.
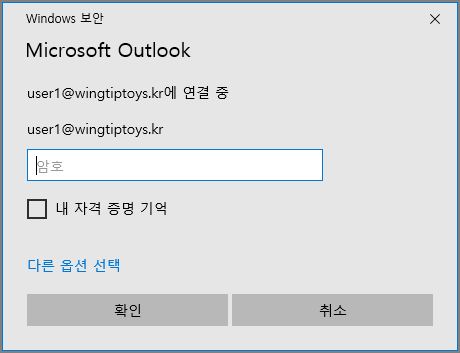
ADFS를 지원하게 되면 아래와 같이 Form 인증 형태로 로그인 창이 나타납니다.

Modern auth in Exchange Server 2019 shouldn't be confused with Hybrid Modern Authentication, which uses Azure AD for modern authentication. In fact, HMA is still the only recommended method to enable Modern auth for all on-premises and cloud users in an Exchange Hybrid configuration. This new feature allows Modern auth use by customers who don’t have Azure AD or aren't in an Exchange Hybrid configuration.
Exchange Server 2019의 최신 인증은 최신 인증에 Azure AD 사용하는 하이브리드 최신 인증과 혼동해서는 안 됩니다. 실제로 HMA는 Exchange 하이브리드 구성의 모든 온-프레미스 및 클라우드 사용자에 대해 최신 인증을 사용하도록 설정하는 유일한 권장 방법입니다. 이 새로운 기능을 사용하면 Azure AD 없거나 Exchange 하이브리드 구성에 없는 고객이 최신 인증을 사용할 수 있습니다.
-> HMA가 이미 설정되어 있으면, Modern 인증을 추가로 설정할 필요가 없습니다.
HMA는 인증기관이 Azure AD이고, Enabling Modern Auth 를 설정하면 ADFS가 인증기관으로 지정됩니다.
HMA는 다양한 플랫폼(Outlook, Mobile 등)을 지원하지만, 단순 Modern Auth 는 Windows Outlook만 지원합니다. -> 연말에 업데이트를 통하여 추가 지원 예정
II. How will Modern Authentication work and is this feature applicable to me?
With Modern auth, users can authenticate to Exchange using ADFS. When Modern auth is enabled for a user, their Outlook client is redirected to ADFS. Users can then authenticate by providing credentials or performing multi-factor authentication. Once ADFS authenticates a user, it generates access tokens. These access tokens are validated by Exchange Server to provide client access to the user’s mailbox.
최신 인증을 사용하면 사용자가 ADFS를 사용하여 Exchange에 인증할 수 있습니다. 사용자에 대해 최신 인증을 사용하도록 설정하면 Outlook 클라이언트가 ADFS로 리디렉션됩니다. 그런 다음 사용자는 자격 증명을 제공하거나 다단계 인증을 수행하여 인증할 수 있습니다. ADFS는 사용자를 인증하면 액세스 토큰을 생성합니다. 이러한 액세스 토큰은 Exchange Server에서 유효성을 검사하여 사용자의 사서함에 대한 클라이언트 액세스를 제공합니다.
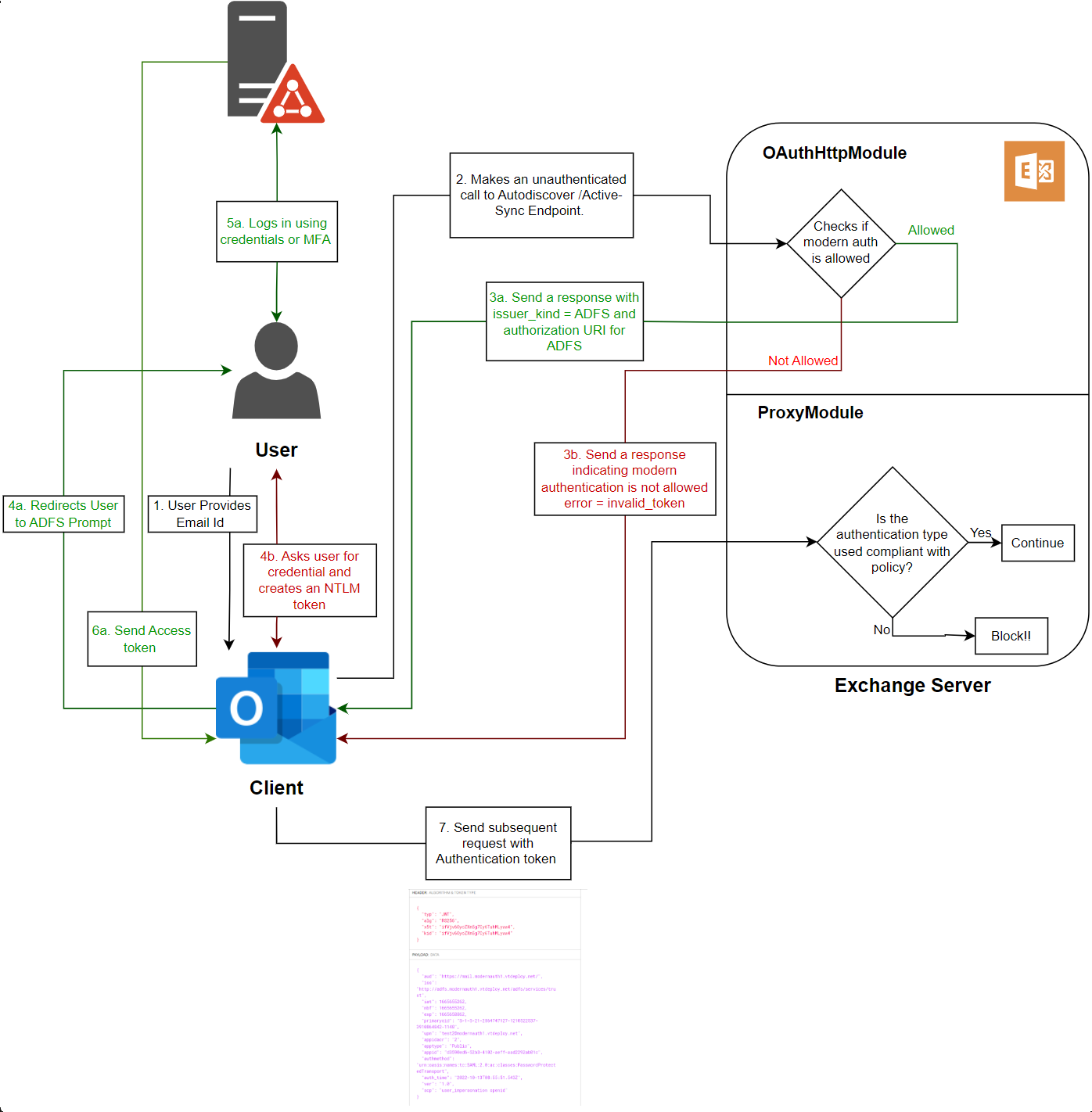
The following diagram illustrates the coordination between Exchange Server, ADFS and Outlook to authenticate a user using Modern auth.
다음 다이어그램에서는 최신 인증을 사용하여 사용자를 인증하기 위한 Exchange Server, ADFS 및 Outlook 간의 조정을 보여 줍니다.
-> Modern 인증이 설정되면, Outlook 연결시 ADFS를 통해서 MFA까지 설정할 수 있음을 설명하고 있습니다.
아래의 다이어그램은 인증 흐름을 설명해주고 있습니다.
III. Prerequisites to enable Modern Authentication in Exchange
Modern 인증을 사용하기 위한 요구 사항은 다음과 같습니다.
1) Exchange Server 2019 CU13 or later
2) ADFS 2019 or later
3) The Outlook build number must be 16327.20200 or later.

Support for other clients such as Outlook on Mac, Outlook mobile, iOS mail app, etc., will be added later.
Mac용 Outlook, Outlook 모바일, iOS 메일 앱 등과 같은 다른 클라이언트에 대한 지원은 나중에 추가될 예정입니다
-> 현재 지원되는 부분은 MAPI 영역만 해당하는 것으로 보입니다. EWS를 이용하는 Outlook for mac, EAS를 이용하는 Mobile은 구분되는 것 같습니다.
4) The Windows client must be Windows 11 22H2 or later and it must have the March 14, 2023 update installed. You can review Windows Update history to verify that KB5023706 is installed.
IV. Steps to configure Modern Authentication in Exchange Server using ADFS as STS
제 테스트 환경은 Exchange Server 2019 CU13이 설치되어 있고, ADFS는 이미 구성되어 있다는 전제하에 진행합니다. Azure MFA 설정이 필요하다면 다음 글을 참고하시기 바랍니다.
2021.12.18 - [Windows Server] - Windows Server 2019. ADFS에서 Azure MFA 설정
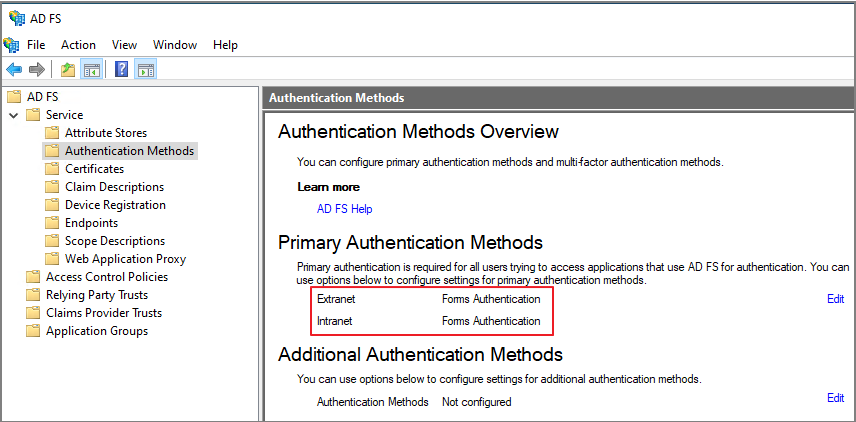
내부망, 외부망 인증방법이 Form 인증으로 설정합니다.
Application Groups -> 우클릭 -> Add Application Group

이름 지정 -> Native application accessing a web API 선택 -> Next

다음과 같이 지정
Client Identifier: d3590ed6-52b3-4102-aeff-aad2292ab01c
Redirect URI
urn:ietf:wg:oauth:2.0:oob
ms-appx-web://Microsoft.AAD.BrokerPlugin/d3590ed6-52b3-4102-aeff-aad2292ab01c

Identifier에 Autodiscover 및 MAPI URL 주소를 입력합니다.

아래의 항목은 우선 Next (나중에 변경할 수 있습니다.)
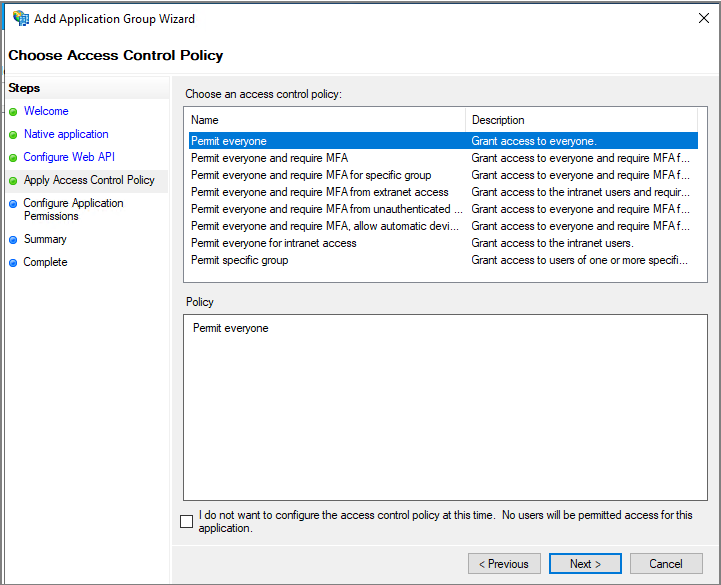
Openid, user_impersonation 체크 -> Next
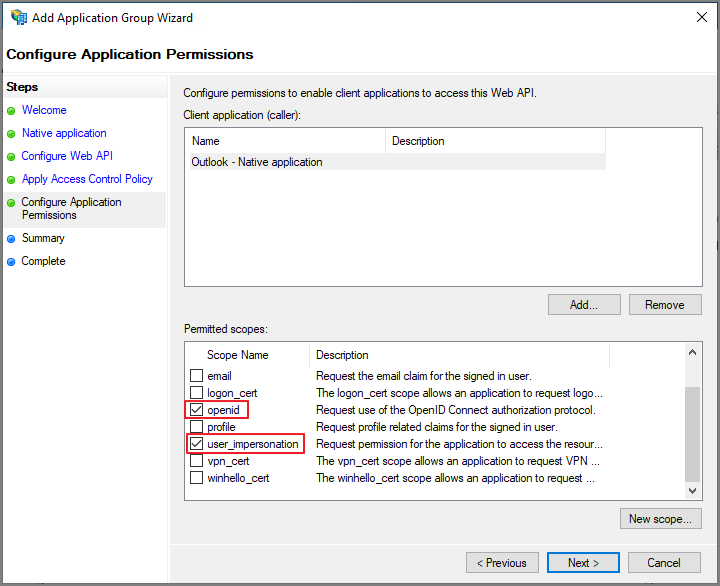
Next
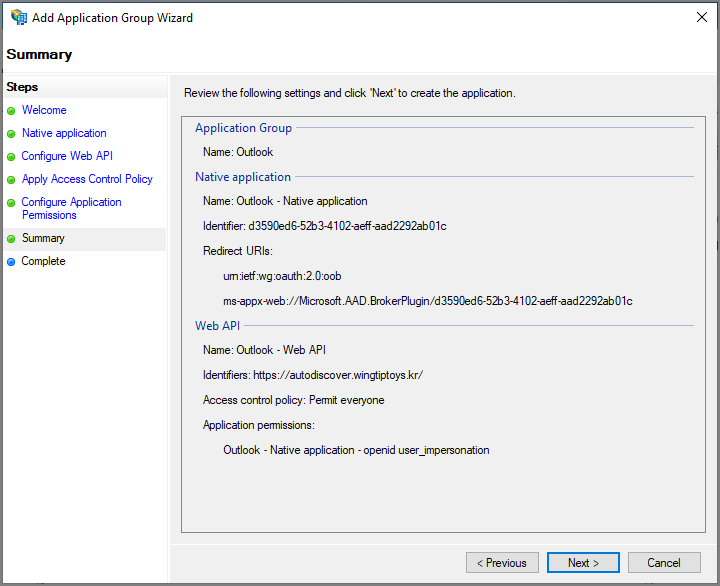
Close

생성된 Application Group 에서 Web API -> Edit

Issuance Transform Rules -> Add rule
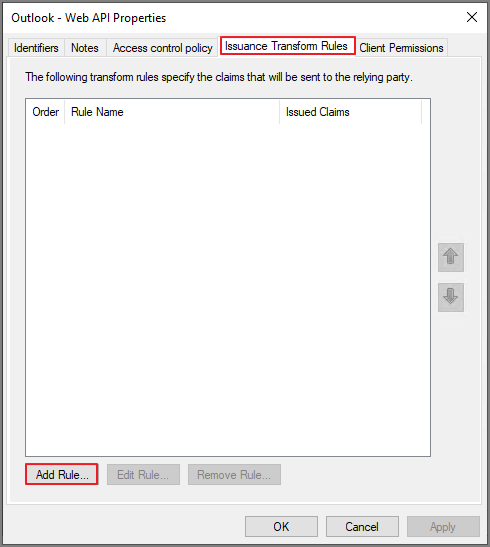
Send Claims Using a Custom Rule -> Next

아래의 Rule을 각각 생성합니다.
| Claim Rule Name | Custom Rule |
| ActiveDirectoryUserSID | c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/primarysid"] => issue(claim = c); |
| ActiveDirectoryUPN | c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"] => issue(claim = c); |
| AppIDACR | => issue(Type = "appidacr", Value = "2"); |
| SCP | => issue(Type = "http://schemas.microsoft.com/identity/claims/scope", Value ="user_impersonation"); |




Rule 생성이 완료되면 다음과 같이 확인할 수 있습니다.

V. Configure Exchange Server to use ADFS OAuth tokens
Exchange Server Powershell에서 가상 디렉터리 인증 설정 확인
Get-MapiVirtualDirectory |fl Identity, *auth*
Get-WebServicesVirtualDirectory |fl Identity, *auth*
Get-OabVirtualDirectory |fl Identity, *auth*
Get-AutodiscoverVirtualDirectory |fl Identity, *auth*



Auth Server 추가 (sts.wingtiptoys.kr 은 ADFS URL 입니다.)
New-AuthServer -Type ADFS -Name MyADFSServer -AuthMetadataUrl https://sts.wingtiptoys.kr/FederationMetadata/2007-06/FederationMetadata.xml
VI. Client-Side Modern Authentication configuration
Client 단에서 ADFS 모던인증을 활성화 하려면 특정 레지스트리 키 값을 추가해야합니다. 아래의 과정을 참고하여 GPO로 설정하는 것을 권장드립니다.
#Add ADFS domain as trusted domain
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\AAD\AuthTrustedDomains\https://ADFS domain/
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\AAD\AuthTrustedDomains\https://ADFS domain

#To enable Modern auth via ADFS in Outlook
[HKCU\SOFTWARE\Microsoft\Office\16.0\Common\Identity]
EnableExchangeOnPremModernAuth=dword:00000001

VII. Test Outlook Client
계정 설정시 아래와 같이 ADFS 로그인 창이 나타납니다.

설정 완료

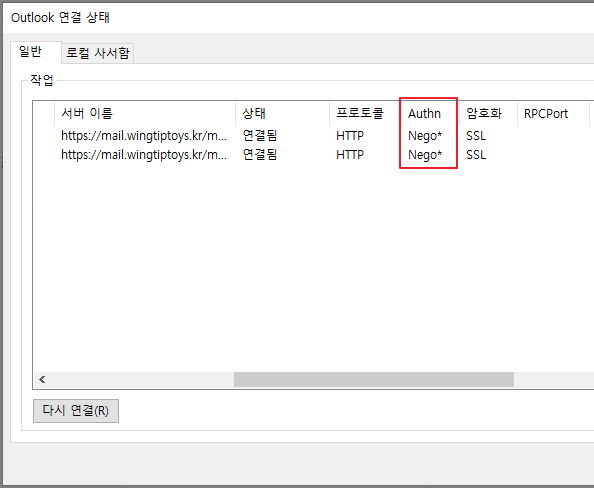
우측 하단의 Outlook 아이콘을 Ctrl 키 + 우클릭
Connection Status

Authn이 Bearer 로 변경된 것을 확인할 수 있습니다.